Most cars these days offer some form of phone syncing capabilities. Usually, though, they don’t offer much support beyond hands free phone and text. Any app support is often native to the software and doesn’t interface with the app on your phone. Map support is either a separate navigation system in the car or limited to direction readout from the phone, with no accompanying visual.

Android Auto give you all these capabilities and more. Although initial native support was small, currently almost 87 2015 cars come with it built in and there are plans to expand that number to almost 150 for the 2017 models. Many major aftermarket headunit brands include Android Auto as well, including Pioneer, Kenwood and Alpine.
Google developed Android Auto to comply with common safety standards including the National Highway Traffic Safety Administration (NHTSA). In order to do this, all apps supported by Android Auto must be checked by Google to ensure that they comply with those standards. They currently list 53 compatible apps on their play store which can be found here. A great example of this safety focus is text messages: no texts are displayed on the screen, instead they are read back to you. In addition voice commands , including “OK, Google” commands, are heavily relied on to maximize its hands free capabilities.
Right now in order to use Android Auto you have to plug it into your car via USB cable. When this happens all interaction is either through your car’s stereo or via voice commands (it’s unclear whether the phone’s microphone can be used for this or if the car has to have one). Google recognized this convenience and announced in May that they would be working providing Android Auto just through the phone. The interface would still look relatively similar, and all the voice commands would remain.
Although the platform is still relatively young, it looks like a promising app for drivers. At a time when distract
 Nextcloud
Nextcloud Gitlab
Gitlab





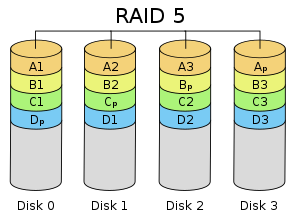 Data can be read very quickly from this array, although write times can suffer because of the need to write the parity data.
Data can be read very quickly from this array, although write times can suffer because of the need to write the parity data.

 d ended up having to get a new one. After a few hours of research and looking through the Black Friday discounts I settled on the Samsung Galaxy S5.
d ended up having to get a new one. After a few hours of research and looking through the Black Friday discounts I settled on the Samsung Galaxy S5.